Passive DNS: A Must Have
In a world of redacted WHOIS, Passive DNS is the game-changing technique that turns a single clue into a map of infrastructure.
Last updated: July 9, 2025

This article was made possible through the support of NameFluent.
NameFluent is a DNS consulting firm co-founded by Chad Los Schumacher (author of this site - Digging DNS) with a mission to help bridge gaps on knowledge on all things domains for entities and organization of all sizes and objectives.
Introduction
Passive DNS was my "game changer" moment.
I first started learning about passive DNS (pDNS) back in 2014 when I gained access to Farsight's DNSDB (now part of DomainTools). Once I fully wrapped my head around what the dataset was, how it worked, and the records it contained, it was an absolute game changer for my work. Suddenly, the internet looked completely different.
Early in my career using this data, I had an investigation involving an individual sending harassing emails and posting defamatory content about a client on a website. The client had a small pool of people they suspected. All we had to go on was the IP address of the harasser. Traditional lookups on the IP were a dead end. But a passive DNS query on that IP revealed a golden nugget: a resolution for vpn.their-business-name.com. One of the business's owners was related to one of the individuals the client suspected. Further pDNS queries on adjacent IPs in the same block (provided by their ISP) revealed other services for their-business-name.com resolving that very day.
We couldn't prove who wrote the words, but we could prove, with high confidence, that the actor was connected to and/or had physical access to that specific business office over a period of time. WHOIS data could never have provided that. This is the power of passive DNS.
What is Passive DNS?
At its core, passive DNS is a historical database of DNS resolution data. Instead of actively querying a nameserver for a current answer (like dig does), pDNS relies on a network of sensors to passively record DNS queries and their responses as they happen across the internet.
These sensors are typically placed on recursive DNS servers (like those operated by ISPs or security companies). As users browse the web, their queries flow through these resolvers, and the sensors record the various resolutions. It is like a log that reads: "At this date and time, example.com was asked for, and the answer was IP address 127.0.0.1."
This creates a massive, searchable archive of how domain names have resolved over time.
A Critical Note on Privacy: You Can't See Who Asked
When investigators first learn about passive DNS, a common question arises: "If it records DNS queries, can I see the IP address of the person who looked up the malicious domain?"
The answer is an emphatic no. This is a fundamental privacy principle of passive DNS collection.
The pDNS providers who operate these sensor networks are in the business of aggregating DNS resolution data on a massive, internet-wide scale, not tracking individual end-users. Their privacy policies and technical architecture are designed to specifically discard or never store the source IP address of the original requester.
The data they provide answers questions of where did records resolve. It does not answer who asked for what. So, as an investigator using a pDNS database, you should never expect to see the specific IP addresses of the individuals whose queries were observed.
However, it's important to remember the fundamental nature of how DNS works: for any DNS query to be successful, the server receiving the query (your recursive resolver) must know your IP address to send the answer back. While the pDNS database is anonymized, the act of making a DNS query itself is not inherently anonymous to your upstream provider. This is an unavoidable factor of the protocol, but it is distinct from the privacy-protected data you find in a passive DNS tool.
Passive DNS vs. Historical WHOIS: What's the Difference?
It's crucial not to confuse passive DNS with historical WHOIS records.
- Historical WHOIS/DNS Records are like finding an old phone book. They are snapshots of how a domain's records were configured at a specific point in time. It's valuable, but it doesn't prove the domain was actively being used or visited.
- Passive DNS Records are like call logs from the phone company. They show that a domain was actually being looked up and resolved by real users. It provides proof of life and context, with valuable metadata like "first seen," "last seen," and observation counts.
At OSMOSISCon in 2017, I gave a presentation that argued with WHOIS data becoming increasingly private due to GDPR, passive DNS needed to become an essential tool for OSINT investigators. "DNS records don't lie", a slide I wrote boldly stated. Systems need them to resolve correctly in order to function. WHOIS records, on the other hand, can be filled with made up non-sense. pDNS offers leads based on hard-to-fake datapoints.
The Power of the Pivot: Using pDNS for Investigations
The true value of pDNS is that it offers new leads you would otherwise never find by just looking at a single domain, hostname, or IP address. The number of "pivot" points can explode rapidly, turning one clue into a map of an adversary's infrastructure.
Pivoting on Nameservers
My personal greatest successes in investigations have come from pivoting on authoritative nameservers. When you find the NS records for a malicious domain, you can then perform a "reverse" pDNS lookup on those nameservers to find all other domains that have used them.
Why is this so powerful? Because an adversary deliberately chose to use those nameservers for their traffic, giving them better control, the ability to monitor or block traffic, or simply to keep their infrastructure organized. If the nameserver is something novel (e.g., ns1.bad-guy-domain.com) and not a generic provider like Cloudflare or a major registrar's default nameservers, there's a very good chance that any other domain using it is related to the same actor. Furthermore, nameserver IPs are often "glue records" in the registry, making them more consequential to change and thus more stable as an indicator.
Pivoting on IP Addresses (and Their Neighbors)
The most common pDNS pivot is a reverse IP lookup. But don't just look at the single IP address; look at its neighbors. In my introductory story, the ISP had given the business a block of 13 IP addresses. By "scanning" (via pDNS lookups, not active port scanning) the adjacent IPs in the CIDR block (like a /29 or /28), you can often reveal other services and domains that belong to the same entity but aren't hosted on the primary IP.
Pivoting on Other Records
You can pivot on almost any piece of data:
- MX Records: Find all other domains that use the same mail server.
- TXT Records: Find other domains that share the same unique site verification code or a specific SPF string (and then pivot on the IP address in the SPF record!).
- Subdomains: A pDNS lookup on a domain can reveal subdomains (
dev,vpn,mail,api) that give you clues about the organization's structure and technology stack. You can then take these subdomains and check them on resources like the Wayback Machine to see what their websites looked like in the past.
Interpreting Imperfect Data and the Art of Analysis
Passive DNS is not perfect; it only contains what its sensors have observed. But this imperfection is also a source of intelligence.
Even if something is seen only once, it existed.
Don't be discouraged by a low observation count. It could mean many things:
- The hostname was very short-lived (e.g., a malware C2 server).
- The service is not frequently used or is not highly targeted.
- The specific resolver network where the sensors are located just didn't see much traffic for it, while another network might have seen a ton.
Conversely, a huge number of observations over a short period might indicate automated traffic, like a botnet checking in. The key is to never dismiss data at either end of the spectrum, but to use the counts as another piece of context for your analysis.
Understanding the Provider Landscape
It's important to know the primary business of your pDNS provider, as it influences the data they have.
- Threat-Focused Providers: Services like VirusTotal, SURBL, and CIRCL are heavily involved in the threat intelligence space. Their pDNS data is often rich for malicious or suspicious domains but may have less coverage for benign, everyday domains.
- Infrastructure-Mapping Providers: Companies like Zetalytics, DomainTools (Farsight) and SecurityTrails aim to provide a much more comprehensive, generic picture of the entire internet. Their goal is often to help defenders understand their own infrastructure footprint as an attacker might see it, resulting in a broader dataset across both malicious and benign domains.
No single provider has a complete view of the internet. Using multiple sources is always the best approach.
Putting It Into Practice: Analyzing Passive DNS from Different Providers
Theory is great, but let's look at some real-world examples using my own domain, diggingdns.com. Below are screenshots from two excellent but very different services: SecurityTrails (which focuses on comprehensive historical data) and VirusTotal (which focuses on security context).
SecurityTrails: The Historical Timeline
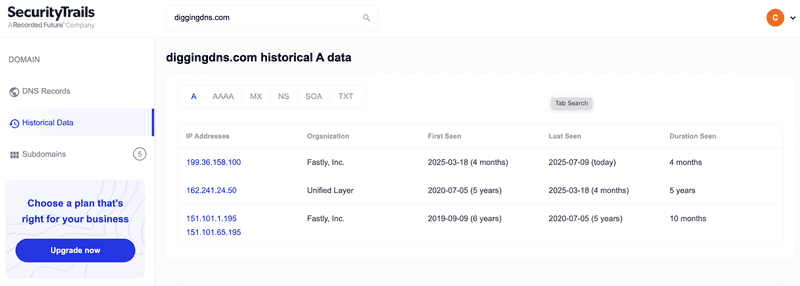
The SecurityTrails interface, under its "Historical Data" tab, presents a clean, chronological timeline of the domain's A records. Let's break down what we're seeing:
- What's Displayed: This view shows every primary IP address (and its associated network organization) that
diggingdns.comhas used, sorted chronologically. - The Data Story: We can clearly see the domain's hosting history. It started on Fastly's network (
151.101.x.x), moved to Unified Layer (162.241.24.50) for about five years, and then recently moved back to a different Fastly IP (199.36.158.100). - Strengths:
- Clarity and Completeness: SecurityTrails excels at providing a simple, easy-to-read historical narrative of a domain's core infrastructure. The "First Seen," "Last Seen," and "Duration Seen" columns are invaluable for understanding how long a domain was associated with a particular IP address.
- Organization Data: Including the organization that owns the IP block (e.g., Fastly, Inc., Unified Layer) provides immediate context about the type of infrastructure being used (a major CDN, a web host, etc.).
- Weaknesses:
- Lack of Security Context: This view is purely historical. It tells you what the IP was, but not whether that IP was associated with malicious activity at the time.
VirusTotal: The Security Snapshot
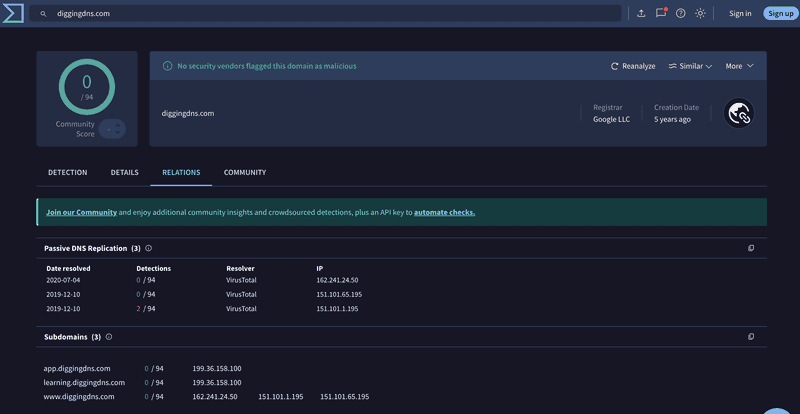
VirusTotal, on the other hand, presents passive DNS data within a broader security context. It's less of a complete timeline and more of a series of security-relevant "snapshots."
- What's Displayed: The "Passive DNS Replication" section shows specific dates when VirusTotal observed the domain resolving to a particular IP address.
- The Data Story: This confirms the data we saw in SecurityTrails, but as discrete events. We can see that on July 4, 2020, it resolved to the Unified Layer IP, and in late 2019, it resolved to the Fastly IPs.
- Strengths:
- Unique Security Context: VirusTotal's superpower is the "Detections" column. This shows you if any of the 90+ security vendors on VirusTotal had flagged that specific IP address as malicious. For
diggingdns.com, the latest score is0/94, which is clean. For a malicious domain, this column would immediately light up, telling you that the domain resolved to a known malicious IP. This is an incredibly powerful and unique dataset for threat intelligence. Remember that these IP addresses are often shared, so the domain being reviewed may not be party to why the IP is flagged as bad. - Subdomain Discovery: This view also clearly lists discovered subdomains and their last-resolved IPs, which is excellent for mapping out a target's infrastructure.
- Unique Security Context: VirusTotal's superpower is the "Detections" column. This shows you if any of the 90+ security vendors on VirusTotal had flagged that specific IP address as malicious. For
- Weaknesses:
- Sampling Based History: It shows you selected resolutions, often those that were submitted for analysis by users or security systems. It is not as truly passive as other sources.
- No Duration Data: This view tells you that a resolution happened on a certain date, but not for how long that resolution was valid (the "first seen" / "last seen" context is missing).
Why You Need Both Perspectives
These two examples perfectly illustrate why using multiple pDNS sources is critical. SecurityTrails gives you the clean, comprehensive historical map of a domain's infrastructure over time. VirusTotal gives you the crucial security context for specific moments in that timeline. By combining the "what" and "where" from SecurityTrails with the "was it bad?" from VirusTotal, an investigator can build a much richer and more accurate picture of a domain's history and potential risk.
Conclusion
In a world of redacted WHOIS records and ephemeral infrastructure, passive DNS is no longer a niche technique—it is an indispensable tool. It allows an investigator to build a historical map of relationships between domains, IPs, and nameservers based on real-world observations. It turns a single, static clue into a dynamic web of pivot points, providing leads and context that are simply unattainable through other means.
